How Exatorial Works: Inside the developer's mind (Part - 2)
In the part 1 of this series, I briefly touched down on the Exatorial Architecture. In this article, I would like to talk more about our data handling strategies.
Data at Exatorial
Every Organization's data is crucial and Exatorial is dedicated to make all data safe. An organisation's data is both a critical asset and a potential liability. Exatorial's unwavering commitment to data security sets it apart as a trusted partner for educational institutions. Through rigorous encryption, fortified infrastructure, granular access controls, and a compliance-driven approach, Exatorial ensures that all data remains shielded from unauthorized access, manipulation, and disclosure.
Permissions Management System
Exatorial's permission management system is built by accumulating knowledge from various state-of-the-art solutions and making them suitable for a SaaS use case. We did our thorough research on various solutions including (but not limited to) Google Zanzibar, Airbnb Himeji, AWS IAM etc.
Our priorities are straightforward from the beginning, "Don't trust anyone" which means everyone is unauthorized, until proven. The basic functional requirements of the system are:
Core/Extensions should declare their permissions (on the Client side) and there should be checks on both client and the server with the configuration provided.
The permissions should be configurable at runtime.
Should scale keeping the Exatorial SaaS infrastructure
Exatorial is made from the ground up to cater to the growing demands of organizations of any size. Consider this example: you are an organization with offices at three different locations (Delhi, Mumbai, and Chennai). An employee at Delhi does not need to view/modify data related to Mumbai or Chennai, until he/she is explicitly given permission to do so. At the same time, the higher executives need to know what happened overall and data that summarizes what happens at all the offices.
These separate data holding private spaces are called as workspaces in Exatorial. The organization should make separate workspaces for all of it three locations to segregate data.
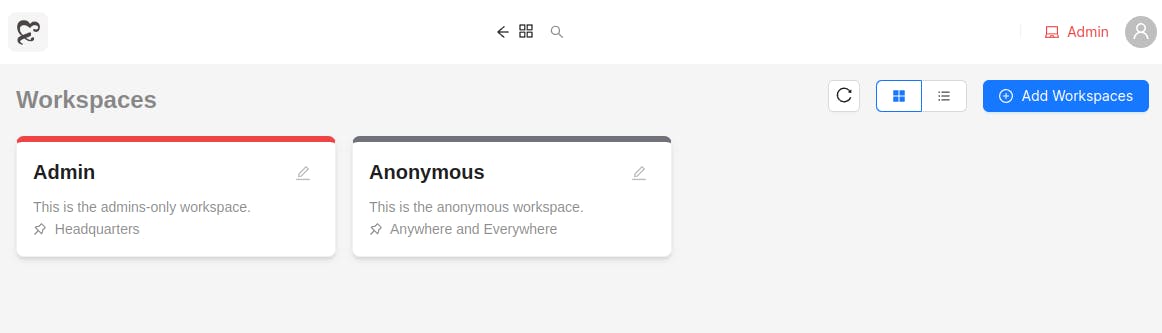
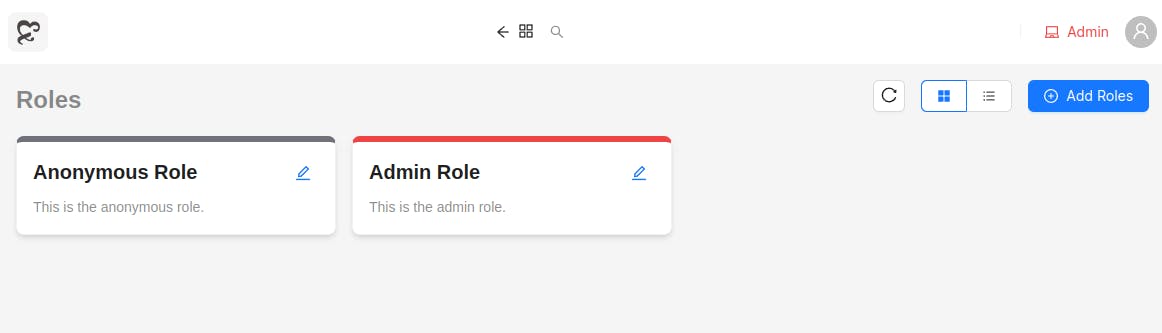
Next, we have roles and permissions, which are scoped to workspaces. Permissions are unique symbols exposed by extensions and the core. Admins can create all sorts of complex permission strategies to best suit the organization's needs. Permissions are of three types:
Allow Self: Allow the given permission on resources created by self
Allow All: Allow the given permission on resources created by anyone
Specific: Only allow the given permission on specific resources
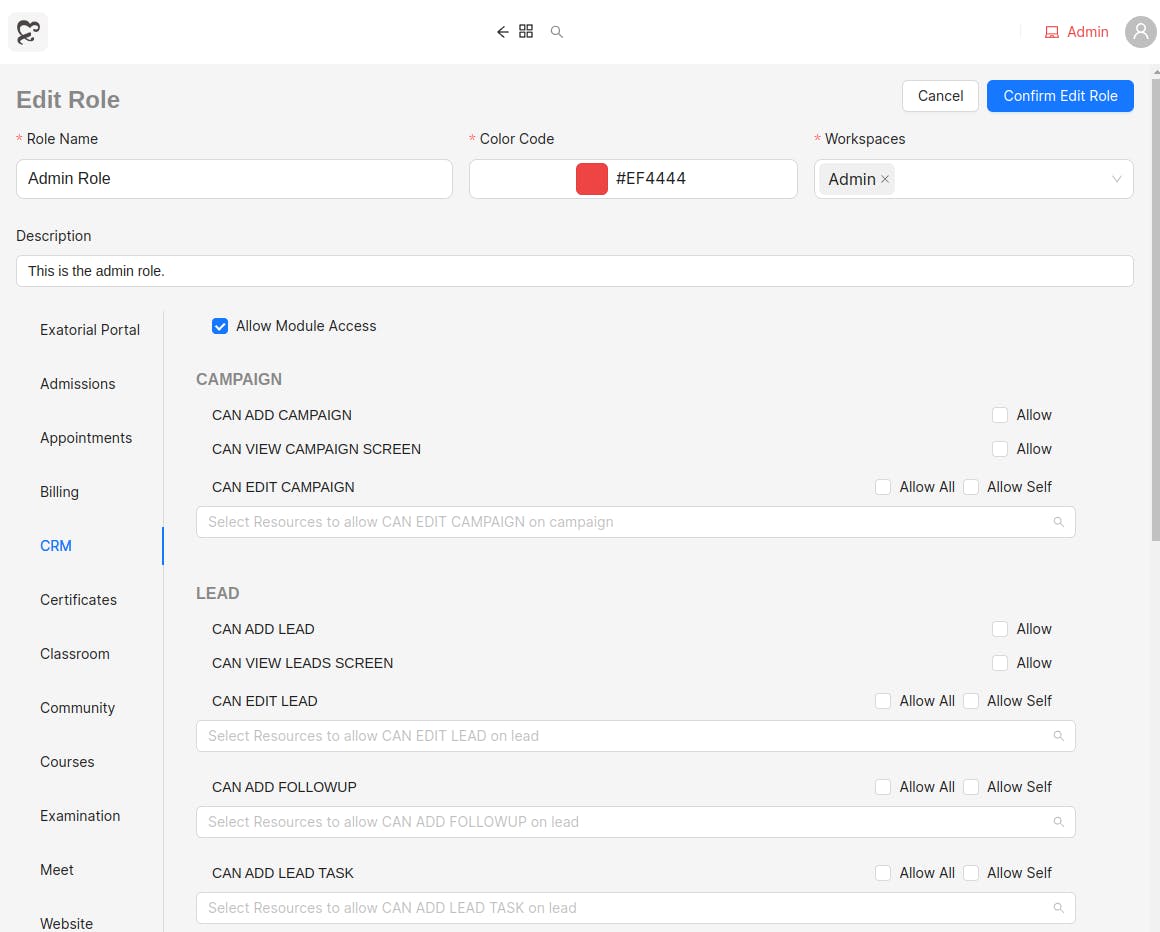
Roles are containers to hold various permissions under a single label. Other than roles, permissions can also be given independently (independent permissions), without creating/modifying any existing role, which caters to the case where you may need very fine grained controls. This is how we make sure your data is safe from any unauthorized access.
Data Transparency
The Exatorial infrastructure is made to handle all sorts of deployment strategies. We truly respect organization's decisions on how and where they store their data and their strategies in terms of data transparency, privacy and security. Currently, we support the given scenarios:
Online (Cloud) deployments: These may be shared (multi-tenant) and/or dedicated (`NO_TENANT_MODE`) based on the organization's decisions
Our databases: We provide the database and we manage the data. Although data ownership is solely to the organization
Your databases: The organization can connect their own instance of mongoDB database and we provide our services on top of those self managed databases.
Offline (On-premise) deployments: Exatorial infrastructure can also run on the servers you own, at your premise completely cut-off from the internet, thanks to its `NO_TENANT_MODE` settings. Although, we don't suggest this strategy due to the complexities involved in on-premise checkups and maintenance.
"You pick and choose what you like and how you want it to be". This principle aligns with almost everything inside Exatorial, including payment gateways etc.
Attack avoidance and Mitigation Strategies
Exatorial servers are properly hardened to ensure security with data stationary or in-transit. We properly make sure certificates/digital-signatures, firewalls, prevention against denial-of-service attacks etc. We make sure we use the best suited tools and techniques for the job to ensure maximum productivity, both for us and our clients. Our API servers, file-storage servers, content-delivery-networks, monitoring and alerting systems etc. all use the best available hardware and software available to maximize performance.
Even in this fortified infrastructure, in case of any unusual event, we do deep research on the strategies used and the mitigation strategies to be used and the preventive measures to make sure attacks like this never happens again.
Compliance
We strictly do not collect any user-specific data-points. Exatorial is a platform intended to be used in places of high security. We employ no means of telemetry at Exatorial. On top of this, we are totally transparent about our data collection and storage strategies as discussed in the data section above.
We will be sharing details about whats and hows of Exatorial in coming posts of the series. Please subscribe to keep yourself updated
